Secure remote database connection
Published:
Introduction
When accessing the remote database (a production database on AWS for example), there are a security hazard you should take into account as describe in the following MySQL docs:
With an unencrypted connection between the MySQL client and the server, someone with access to the network could watch all your traffic and inspect the data being sent or received between client and server.
….
By default, MySQL programs attempt to connect using encryption if the server supports encrypted connections, falling back to an unencrypted connection if an encrypted connection cannot be established.
…
MySQL supports encrypted connections between clients and the server using the TLS (Transport Layer Security) protocol. TLS is sometimes referred to as SSL (Secure Sockets Layer) but MySQL does not actually use the SSL protocol for encrypted connections because its encryption is weak
It means that if your server don’t use TLS protocol, by default MySQL uses unencrypted connections between the client and the server. Thus, if your data is valuable, you should secure all traffic transfer over network to prevent any possible attack.
There are several options including:
- TLS/SSL protocol
- VPN
- SSH tunnel
I don’t know how to configure the first two, haha and this article will guide you over the third one option.
SSH tunnel/port-forwarding
What is an SSH tunnel? (According to ssh.com)
SSH tunneling is a method of transporting arbitrary networking data over an encrypted SSH connection. It can be used to add encryption to legacy applications.
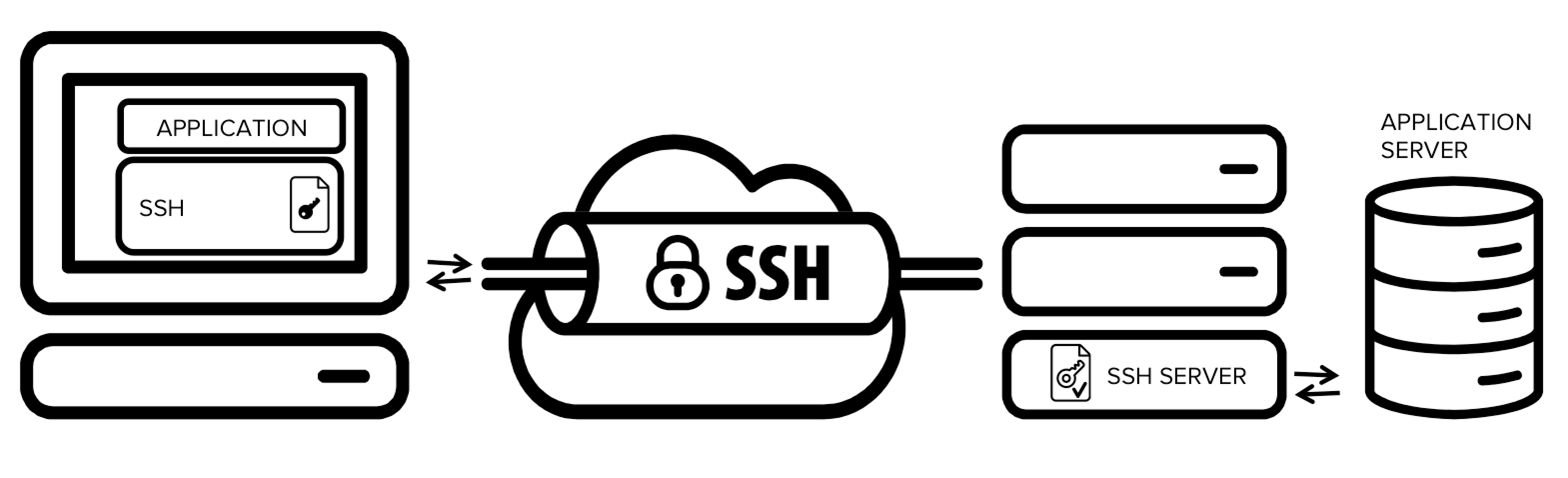
Tunneling or forwarding a port allows you to encapsulate TCP traffic inside a SSH connection.
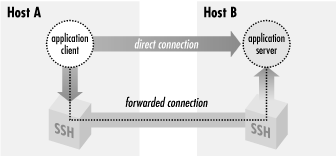
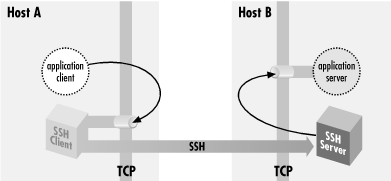
When you connect to a remote database instance, an SSH Tunnel will link a port from your working computer to a port on your remote host and encrypt that connection. Any data transported between your local machine and the remote server will go through the SSH first, be encrypted, then passed to the other end securely.
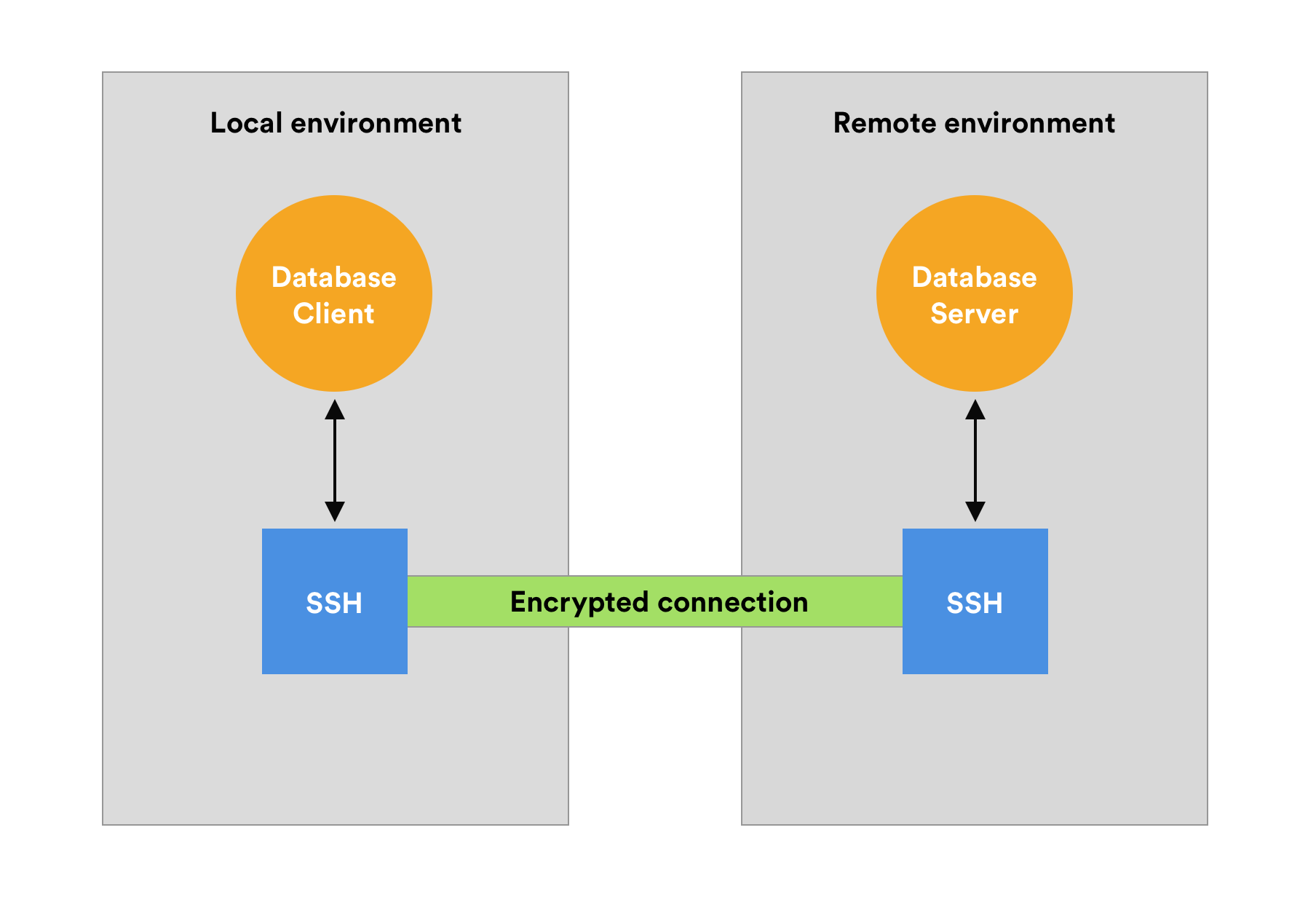
Setup SSH tunnel/local port-forwarding
Using DataGrip
- Create new database connection

- Go over SSH/SSl tab, check the box Use SSH tunnel

- Configure your own ssh tunnel

- Create new database connection
Via command line
Maybe you want to configure the previous steps (2 & 3) via command line instead using local port-forwarding
ssh -i ~/.ssh/id_rsa -N -f -L 27017:localhost:27017 logbasex@3.16.06.97
References
- https://security.stackexchange.com/questions/3958/risk-of-configuring-mysql-for-remote-access-with-a-dynamic-ip-address
- https://tableplus.com/blog/2019/08/ssh-tunnel-secure-database-connection.html
- https://dev.to/samuyi/the-how-to-of-ssh-port-forwarding-1f4e
- https://www.ssh.com/academy/ssh/tunneling
Thank for reading.